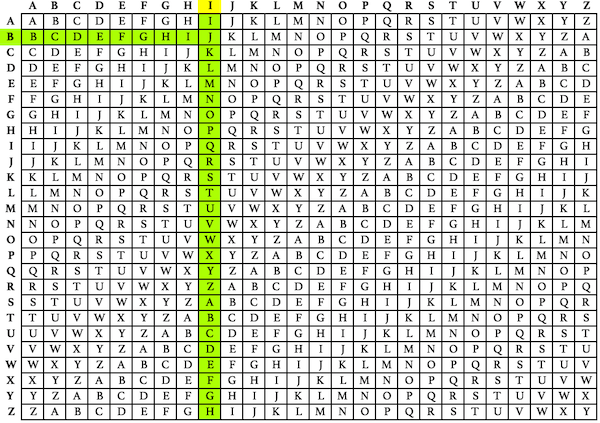
inch ✌🏻 on Twitter: "I typed zjylht into a caesar cipher decoder and scream is one of the results. I guess we're on the right track?… "
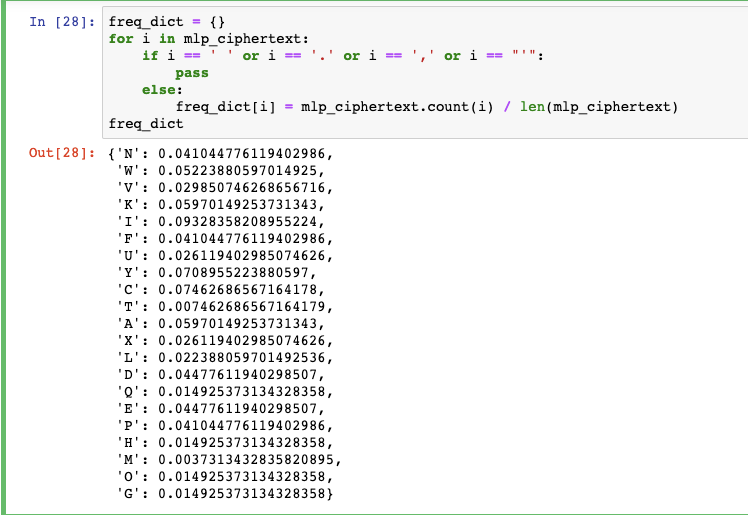
Breaking My Little Pony: Frequency Analysis for Breaking Ciphers | by Jonathan Keller | Towards Data Science





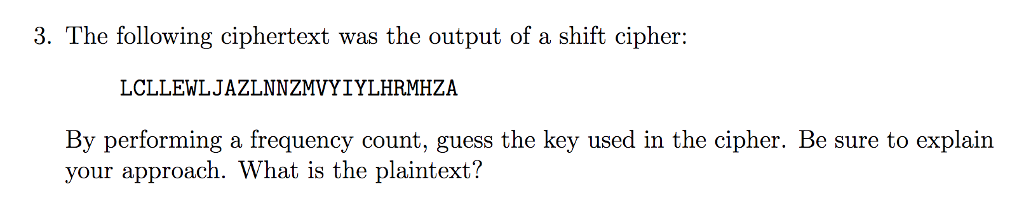



.png)





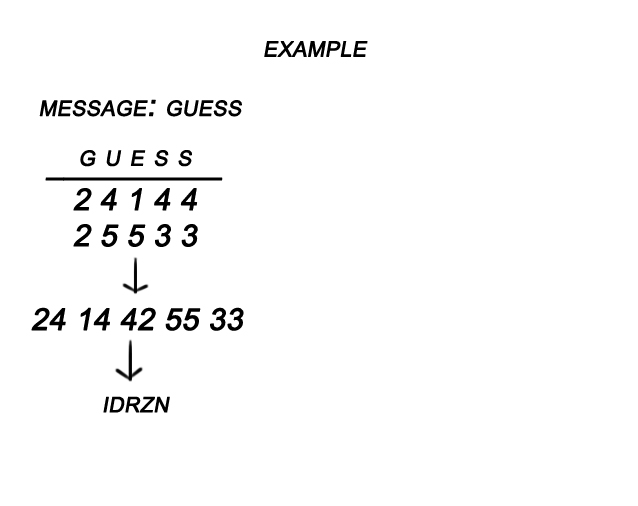
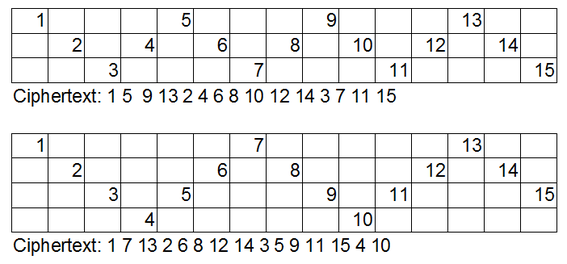
![PDF] The New Heuristic Guess and Determine Attack on Snow 2.0 Stream Cipher | Semantic Scholar PDF] The New Heuristic Guess and Determine Attack on Snow 2.0 Stream Cipher | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3157dccb4710a1bb9270d74f7018a49406223361/5-Table4-1.png)

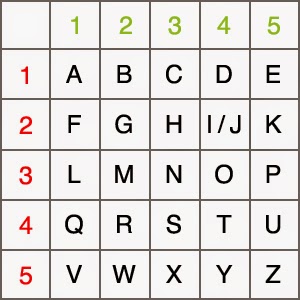
![PDF] An Improved Guess-and-Determine Attack on the A5/1 Stream Cipher | Semantic Scholar PDF] An Improved Guess-and-Determine Attack on the A5/1 Stream Cipher | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/adf3978659c103dc700f1db3826714ca8098d0e5/2-Figure1-1.png)